Being a shipping IT professional can be frustrating. You recognise the need to invest in further cybersecurity, but your management team still treat it as a “compliance problem”. But perhaps this is a result of the way cybersecurity has been presented to leadership. The dialogue needs to change. IMO 2021 could offer a unique opportunity to reposition cybersecurity as an important enabler of the wider business objectives. Follow us on LinkedIn to get exclusive access to a series of articles and tools designed to power up your journey toward managing the cyber risks on-board your vessels.
At our recent virtual conference – CyberSecure at Sea – we asked ~120 shipping IT professionals what was holding them back from rolling out cyber security controls. ~50% pointed toward the struggle with providing their management teams the confidence that they are spending wisely on cyber security or that investing in additional resources to manage cyber risk is required at all. It is clear there is a misalignment between what IT professionals know is needed and what leadership believes is the risk.
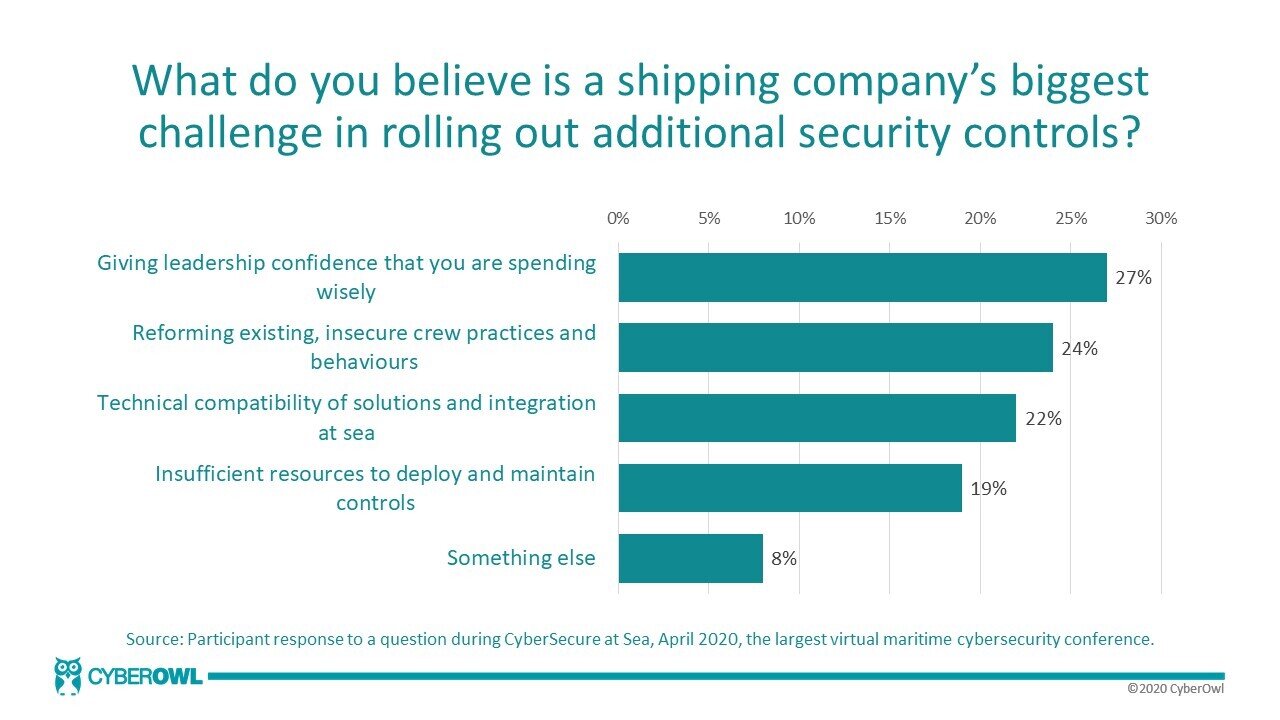
Management teams in shipping believe cyber security is mainly a “compliance problem”
This is frustrating for the IT professional. But it isn’t really a surprise.
Management’s main concerns are driving up revenue and driving down cost. Maximise chartering at minimal expense. To run a tight ship, any investment that cannot visibly drive either of these twin goals is deprioritised. If the link is not clear, they don’t believe it or they don’t understand it, investing in it is a luxury. So the responsibility falls on the CIO or IT manager to help leadership understand the need and urgency.
But shipping IT professionals still find themselves stuck in a dialogue with management about how to do the bare minimum in order to comply with IMO 2021, instead of how to take steps to properly cybersecure.
From our discussions with shipping IT professionals, we find only 20% are actively engaging with their management to align cybersecurity strategy. In over 65% of cases, the dialogue is either focused purely on compliance or related to purchasing specific cybersecurity solutions. This means that for every 100 interactions that IT professionals have with their management team, 65 of them are either discussing compliance or a point solution.
Interestingly, none of the shipping IT professionals we speak to have a relationship with management where they agree to an annual budget and make the day to day decisions around cybersecurity strategy and tactics. So management are making decisions on what cybersecurity controls to put in place on a case by case basis, rather than the IT professionals.

This is why cyber security in shipping is still commonly treated as a “compliance problem” – it is being presented as one.
This mindset is based on false assumptions
The most dangerous one is that shipping is not a targeted sector. If you still don’t believe the threat landscape is shifting, then just look at the data – just within the first 5 months of 2020, there were public announcements of cyber attacks on MSC, Anglo Eastern, OSM and twice on Toll Group. While the amount of losses in revenue or remediation costs remain guarded secrets, they have all admitted to significant interruptions in operations.
Another false assumption is that we can achieve vessel digitalisation and worry about cyber security later. The evidence is clear that this simply isn’t the case. Just to cite one example, a common assumption is that you can maintain separation of the business, crew and OT networks. So it should be impossible for an attacker to compromise a crew asset, then use that foothold to attack a critical business workstation or OT system.
In reality, in ~80% of vessels CyberOwl has deployed on, we find assets connected to the business network that the IT manager knows nothing about. They haven’t identified them in their inventory, have no idea of their nature, did not sanction a connection, had no way of controlling or disconnecting them remotely. Sometimes it is not just 1 or 2 such assets, but 10s of them. In several cases, these unauthorised connections were later discovered to be OT devices linked to a bridge system, the engine room or auxiliary power system.
The relationship between IT and management needs to change. IMO 2021 is an opportunity to get “air time”.
IMO 2021 presents a window of opportunity. Management teams have no choice but to make sure their fleet has a cyber risk management system that complies. Instead of approaching the dialogue as a compliance issue, this is the opportunity to frame cyber security as a business issue – an enabler to deliver overall business priorities. Whether this is business efficiency, vessel performance optimisation, remote control and management or crew welfare.
There are useful examples in recent history of leveraging compliance to strengthen overall cyber risk management. According to analysis by Marsh, companies successfully used GDPR as a catalyst, with 78% investing more in cyber security en route to GDPR compliance. A key finding in a 2019 UK government report was that as a result of GDPR, there was a significant increase in the number of businesses putting in place quarterly updates with senior management on cybersecurity, intensifying cybersecurity training and enhancing cybersecurity policies. Essentially, where the opportunity was taken, GDPR had a positive effect in improving executive attention that prompted the related investments.
This window of opportunity won’t last forever. Don’t squander it.
So how do shipping IT professionals make the most out of IMO 2021?
-
Shifting the emphasis of the discussion with management is an important start. Turn the conversation from “what we need to do to comply” to “how does cybersecurity support the way we want to work going forward.” For example, the need for better remote access control becomes less about the fact it is an IACS recommendation, but more because it reduces the need to get an engineer onboard the vessel.
-
Use IMO 2021 as a catalyst for working more closely with your colleagues in technical, operations and quality. Get a good understanding of their ambitions for improving performance and reducing costs. Use this knowledge to demonstrate how cybersecurity could help them achieve that securely. Link your cybersecurity initiatives with their cost-savings or revenue-gain figures.
-
Quantify the risk within the context of these wider business objectives. Help management visualise the potential loss due to a cyber attack. But make this real to your own organisation and its digitalisation ambitions, rather than using high-level industry report figures. There are various well-recognised methods for quantifying the cyber risk to an organisation. One approach we like using at CyberOwl is the FAIR methodology.
-
Define some key cybersecurity metrics to start collecting and tracking. Begin with a pragmatic, small number that won’t drown your resources. At minimum, these should measure the volume of system outages, volume of cyber incidents and some aspect of usage policy abuse, misconfigurations or suspicious behaviour. Gather benchmarks on these metrics from a friendly cybersecurity advisor or a collaborative network of other shipping IT professionals. Present the trends and benchmarks to your management, clearly explaining their implications.
-
Lean on your vendors to help you inform your cybersecurity strategy. It is part of the value and service they bring to you. When you perform trials, treat it as a learning exercise, not just a procurement exercise. Clearly set out what you are trying to learn about your current cybersecurity posture, where the risks are and how you are currently managing them. Share this “list of learning points” with your vendor. They should be helping you learn, rather than just proving to you their cybersecurity product is better than the competition.
Finally, it doesn’t need to be a huge transformation programme. Start small and simple. Make some changes. Measure the improvement. Share any good news and small wins. Repeat.
How are you engaging with your management on IMO 2021? Sign up here to get your free consultation on how to reposition the dialogue with your management team.
We are developing a series of practical advice blogs and tools that are free to access and designed to help fleet operators start or “power up” their journey to managing the cyber risks to their vessels. Check out the other blogs in this series and follow us on LinkedIn to be updated on future blogs and tools.


