Monitoring is the backbone of good cyber risk management. If you don’t know what assets you have and can’t see what is happening to those assets, then you can’t respond properly if they are under attack. But some fleet operators struggle to justify the budget until they better understand the volume and severity of cyber risks they’re exposed to – a vicious cycle, where lack of visibility leads to lack of action. Shipping IT managers can break out of this vicious cycle and implement some basic cybersecurity monitoring. This article sets out some practical guidance to get started. The rationale is clear: even some basic monitoring and a response plan makes your vessel significantly harder to attack than the next one. Sign up here to get exclusive access to a series of articles and tools designed to power up your journey toward managing the cyber risks on-board your vessels.
Today’s reality in shipping: virtual blindness
Ask most shipping IT professionals if they are able to gain visibility of their vessel networks and cyber risks and most of them will openly admit they can’t. At our recent virtual conference – CyberSecure at Sea – we asked ~120 shipping IT professionals the most important lesson that business continuity plans under lockdown has taught them about cybersecurity.
Nearly 75% of them admitted to a lack of understanding of their vessel networks and devices – 36% had insufficient central visibility and 38% found a lot more IT, connectivity and shadow IT than they realised was onboard.
So most of the time, most fleet operators aren’t confident what they have on their vessels, how these are connected to the (supposedly) separated OT and Business networks, what vulnerabilities they create and how cyber threats are propagating across them.

Visibility is the backbone of good cyber risk management
This lack of visibility won’t do. No matter what cybersecurity framework you choose, maintaining visibility is commonly identified as a critical capability. If you don’t know what assets you have, then you can’t manage them. And if you can’t see what is happening to those assets then you can’t respond appropriately if they are under attack.
The rationale for increasing your visibility of vessel networks and devices is clear:
-
It helps you understand what vulnerabilities are being created, even if unintentionally.
-
It provides you some assurance that OT and other critical systems and networks are actually separated and have some layer of protection.
-
It enables you to focus and prioritise actions in your cyber risk management.
-
It helps you avoid missing a cyber security incident (happens more frequently than you might expect).
-
It enhances your ability to detect cyber incidents as early as possible.
-
It directs you towards a tailored training and awareness programme. (See our previous article on helping your crew cyber behave)
With visibility comes the ability to perform cybersecurity monitoring
The vast majority of cyber attacks are opportunistic. The attacker is feeling their way around your network or deploying malware in the hope that they hit some asset of value. Even some basic cybersecurity monitoring, along with a solid response plan for acting on the intelligence it delivers, will make it significantly more difficult for the cyber attackers to be successful.
In short, it makes your vessel significantly harder to hack than the next one.
The BIMCO Guidelines on Cyber Security Onboard Ships recognises this and explicitly recommends it. IACS Recommendation on Cyber Resilience No 166 (IACS No 166) also sets out a series of Technical Requirements on cybersecurity monitoring.
Effective monitoring should enable detection of cybersecurity risks and also enable an effective response. We recommend that the monitoring should answer at least these three basic questions:
-
What has just happened?
-
How bad is it?
-
What should we do next?
So if cybersecurity monitoring is obvious, why isn’t shipping doing it?
Monitoring and detection are arguably the most challenging of the NIST framework functions when it comes to shipping. Firewalls and antivirus are reasonably well understood and easy to justify the budget, but getting approval to invest in cybersecurity monitoring can be a tougher sell internally.
The reality is that until you get some idea of just how complex your networks are, the volume and severity of cyber risks you’re exposed to and the level of bad behaviour you are trying to stop, it is difficult to make a business case to your management team. (See our previous article on leveraging IMO 2021 as an opportunity to improve engagement with management teams on cybersecurity) The current lack of visibility means shipping IT managers have no idea the extent of the cyber risk to their vessels. This triggers a vicious cycle – lack of visibility leads to lack of action.
If there is no budget to buy, then start by exploring DIY
One way to approach this is to set up a basic cybersecurity monitoring yourself. If paying for a solution is not an option, then start simple and work with the existing data you have. Get some basic visibility. Learn from it. You will be surprised how taking some basic monitoring steps can provide preliminary visibility of the cyber risks to your fleet.
As you progress, you can then decide how best to roll out a more permanent plan and whether or not that involves bringing in a solution provider.
Full disclosure: CyberOwl is one such solution provider, but that isn’t the point of this article. The rest of this article is to provide some guidance to help you establish your own basic cybersecurity monitoring for your onboard vessel systems. These should all be achievable, at least partially, by most shipping IT teams.
Four steps to establish cybersecurity monitoring (along with some shipping-specific challenges to watch out for)
Step 1 – Review your available data sources
The days of routinely turning off auditing or redirecting logs to /dev/null are a dim and distant memory. When you review what data sources are available, you will most likely find a number of information sources being collected by default across your fleet. However, there may be some variation in retention policies and logging granularity, which may need some reconfiguration.
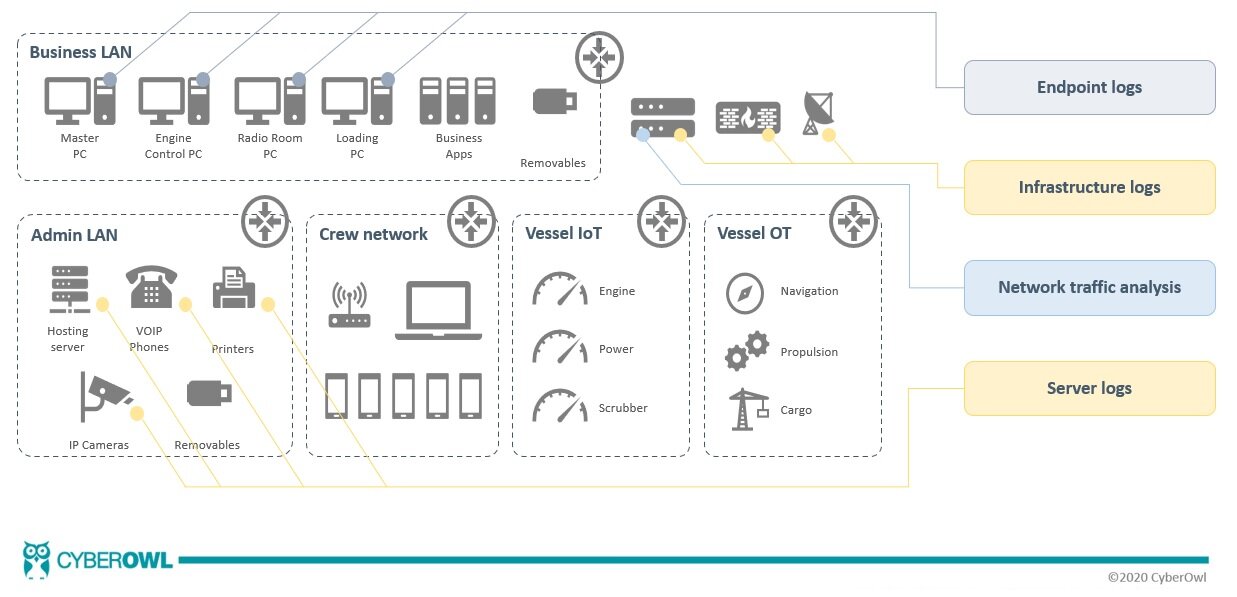
Typical sources on vessel systems:
-
Endpoint logs: logs from the endpoints on your Business VLAN such as Windows Event Logs, Windows Defender or logs from your antivirus of choice.
-
Remote access logs: any of the applications you use to gain remote access to the workstations and servers on your vessel such as TeamView, LogMeIn or Microsoft Remote Desktop Service will keep a record of both successful and unsuccessful connection attempts.
-
Infrastructure change logs: typically, routers, switches and firewalls will routinely keep an audit trail of the changes that have been made to their configuration.
-
Network traffic analysis: details of inbound and outbound requests that are being denied by work the firewall and proxy server respectively will be recorded and logged. It is also relatively simple to build up a pattern of the routine communications between devices on your network through automating open source tools such as Snort and NMap.
-
Finally, if you run DHCP servers don’t overlook the logs from these.
Step 2 – Choose which data to generate, retain and analyse
Collecting and reviewing the output of your logs can be time-consuming and laborious, so it’s important to be selective. Focus on the questions you’re trying to answer.
In our experience, here are 5 particularly meaningful cybersecurity monitoring questions to get started with in shipping:
-
Am I seeing devices appear on the Business network or OT networks that I don’t recognise?
-
Am I seeing a device routinely connected to the Crew LAN pop up on the Business network? If so, why so?
-
Are removable devices being used on the vessel in contravention of policy?
-
Am I seeing suspicious remote access to the vessel’s business network or OT network?
-
Am I seeing unusual communication patterns between the machines on my business network?
By and large, these questions can be answered by analysing the data sources identified in Step 1. Clearly a sophisticated cybersecurity monitoring setup would be hunting for a wider range of threats. But these 5 questions are a good start for most vessel networks. Over time you can always supplement these questions, as you become more familiar with the threats you are actually seeing.
Step 3 – Establish a way to retain and store your data
Your servers and endpoints will have built in mechanisms that handle the rotation of logs to ensure that you do not run out of disk space locally. This means that old logs could potentially be overwritten before you have reviewed them.
Note that if you are collecting any sensitive personally identifiable information (PII) then you will have privacy issues to contend with that are beyond the scope of this article; our recommendation would be to avoid this if you are going down the DIY approach.
It will probably make sense to store the data centrally for easy access (e.g. for investigative analysis). If you go down this route, it makes sense to compress and encrypt before transmission. Most logs compress well and you could design 80-90% reduction in size of the raw log.
Make sure that retrieving the data for review can be done without impacting the operational efficiency of the vessel.
Incidentally, collecting and retaining event logs ticks off elements of Technical Requirements 7.3.6 and 7.3.7 in IACS No 166 – a bonus!
Step 4 – Validate your pipeline is working and establish an understanding of your baseline.
Validate your logging capability is working as intended. You may find your logs are incomplete, incorrect or stop arriving centrally. A DIY solution can take some time to bed in but should not be technically difficult to do.
Review your logs on a regular basis. This will help you achieve a couple of things. Firstly, it will help build an understanding of the baseline behaviour of your vessel network and assets. For example, in our experience, IT managers are often astonished at how much traffic there is between the vessel IT and OT networks that are frequently assumed to be air-gapped.
Secondly, it is very important that you regularly review your logs. If you fail to do this then although you would have built a very useful resource for a post-incident forensic investigation, you will not meet your original objective of proactively discovering intrusions; automation is your friend here, again start simple and build up your scripts into something more advanced overtime.
Visibility is useless without response
All this foundational work to increase visibility of your vessel networks goes to waste if you don’t have a response plan to deal with an incident.
Arguably the single most important thing you can do next is to establish a clear and easy-to-follow playbook for your crew to respond to any cyber incidents detected. We have to accept that the officers’ and crew’s primary responsibility is the safe operation of the vessel. There is unlikely to be a highly skilled cyber security analyst on board. So your response playbook for the crew needs to be very simple and clear on the recommended action, even if this is to contact the shoreside team urgently.
Establishing basic cybersecurity monitoring should be achievable by most shipping IT teams. Sign up here to get your free consultation on how to establish a more robust cybersecurity monitoring capability.
We are developing a series of practical advice blogs and tools that are free to access and designed to help fleet operators start or “power up” their journey to managing the cyber risks to their vessels. Check out the other blogs in this series and sign up here to be updated on future blogs and tools.


