It’s just compliance, isn’t it? It’s easy to conclude that Fleet IT are mainly concerned about complying with IMO 2021 and ensuring vessels aren’t detained due to inadequate cyber risk management. But it turns out the concerns run deeper.
The shipping sector needs all the help it can get on cyber security. So at CyberOwl, we have been running workshops and developing a free toolkit to help the shipping community take practical steps to shore up cyber defences. To stop talking and start doing. Turn theory into practice.
So far the workshops have proved popular. Around 100 have actively participated in a series of closed-door, Chatham House, practical sessions to tackle a range of challenges from risk assessments, to cyber incident playbooks, to designing cybersecurity KPIs. Participants are expected to actively contribute, support and challenge each other in order to maximise value for all.
These workshops have fostered a safe space for sharing key concerns for collective problem-solving and knowledge-sharing on best practices. The discussions have raised some interesting trends and insights into the cybersecurity issues that are keeping the Fleet IT Manager up at night.
No confidence in readiness
The documentation is broadly in place. Cyber policies and SMS have mostly been written up to meet the IMO 2021 deadline although quality varies: Some fleet operators have thought about the roles, responsibilities, technologies and processes in their cyber emergency response plan. Others have simply borrowed template documentation, perhaps from a different fleet operator, and are hoping to tick an inspector’s box with minor changes.
Either way, the overwhelming majority of Fleet IT Managers that attended the workshops still had doubts whether their cyber response plans in their documentation will work in practice. Most were yet to actually test their plans. None could confirm that their cyber incident response plans had been incorporated into the regular vessel safety drills.
On a positive note, some have done some training on cyber incident response, albeit the training has primarily been focused on the shoreside teams rather than the crew. And yet despite this, there are still concerns about the readiness of shoreside teams.
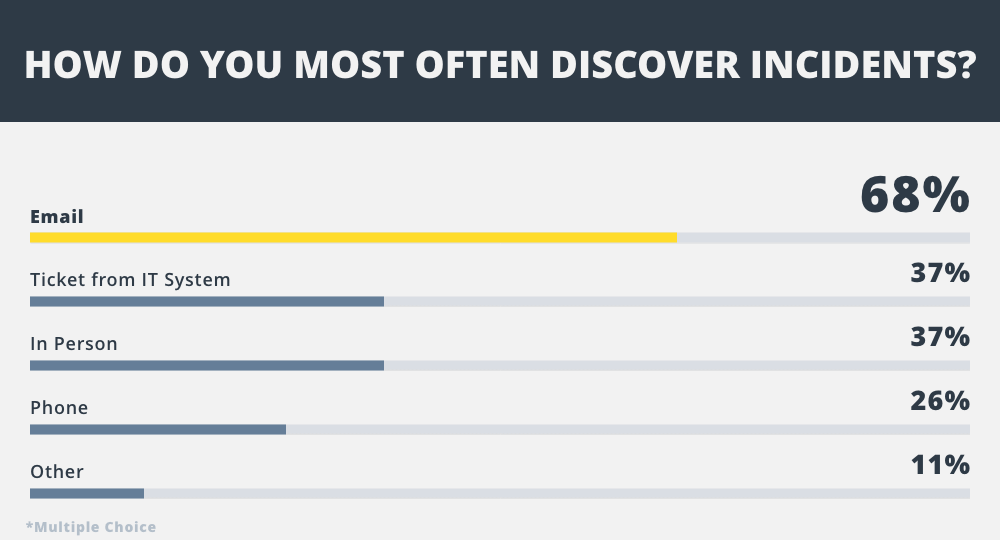
Nearly 70% of Fleet IT Managers expected to learn about a cyber incident via email from the crew. It’s worth reading that sentence again to consider the implications: Obviously, it means that incidents are frequently being missed by the IT team’s own systems or that monitoring and alerting systems are simply not in place.
But it also means that when a future cyber incident takes down the email system then the alert might not get through at all. The IT team may never know about the issue, at least not until an IT engineer boards the vessel and physically spots the issue.
Nearly 50% of fleet operators feel unprepared to engage their supply chain in the event of a cyber attack. In a sector that is a fundamental part of the global logistics supply chain, the ripple effects of not being able to quickly alert your suppliers, customers and port of call in the event of a cyber attack could escalate and domino-effect very quickly.
Nervousness in making prioritisation decisions
There simply isn’t enough time nor skills nor budget. Fleet IT is invariably resource-constrained. A separate discussion is needed about the desperate need for more investment to survive in a sector that is increasingly digitalising, let alone thrive. But for now, this is the reality. So Fleet IT teams know they need to prioritise.
However, making decisions on which risks to prioritise mitigations for and which to ignore is a daunting prospect for an IT Manager. This is even harder for those that have to stray from their core competencies in IT and infrastructure operations, to cyber risk management – which is a new area for the majority of fleet IT engineers. There is an increasing number of maritime cyber security guidelines and notations out there that recommend a long shopping list of mitigations for cyber risks to shipboard systems. A rough estimate suggests that to roll out all the risk controls recommended in the BIMCO Guidance for a fleet of 30 vessels alone would require a permanent team of 3-4 cybersecurity professionals just to deploy, maintain and continuously improve them. Most fleet operators struggle to make that level of investment.
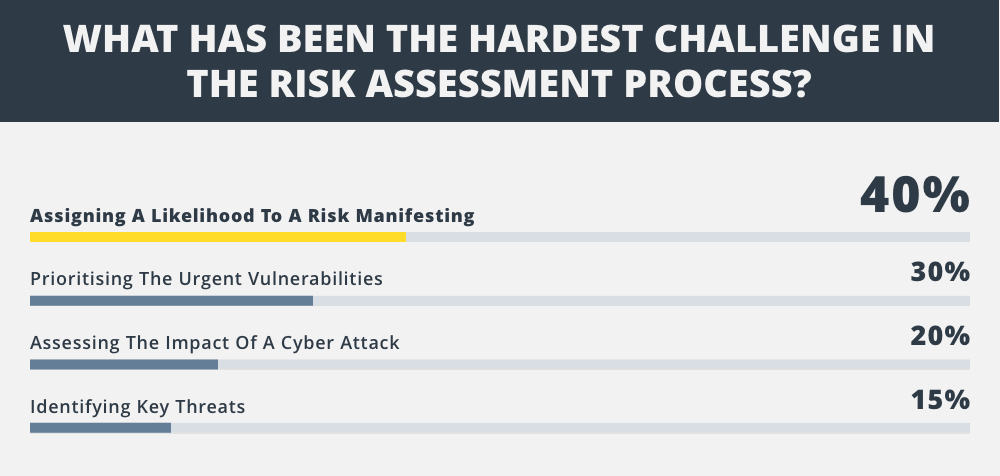
In our workshops, we uncovered that Fleet IT teams find it difficult to assign likelihoods to risks. They are also really struggling to qualify which vulnerabilities are the most important to address. To make matters worse, shipboard software, particularly on OT systems, is not updated frequently if at all. So if you’re using Windows 7 on your shipboard systems, which Microsoft is no longer supporting, performing a vulnerability scan to report a long list of common vulnerabilities in those machines is just not useful.
A better approach is to focus on exposures and design mitigations for those. How does local access work on those systems? What about remote access? What level of data access is available? And how does that impact the likelihood of those vulnerabilities being exploited?
Significant blindspots remain
The responsibility for whole cyber security across the entirety of shipboard systems is still hazy. From a technical standpoint, it falls in the cracks somewhere between the Fleet IT Manager, Technical Manager, system manufacturers and integrator.
Internally, while the Technical Manager has control over decision-making and management of the OT systems of the vessel, it is often the Fleet IT Manager that is better technically qualified to design a cybersecurity architecture and operations for the vessel. However, cross-team consultation and risk assessment is still not a well-oiled machine.
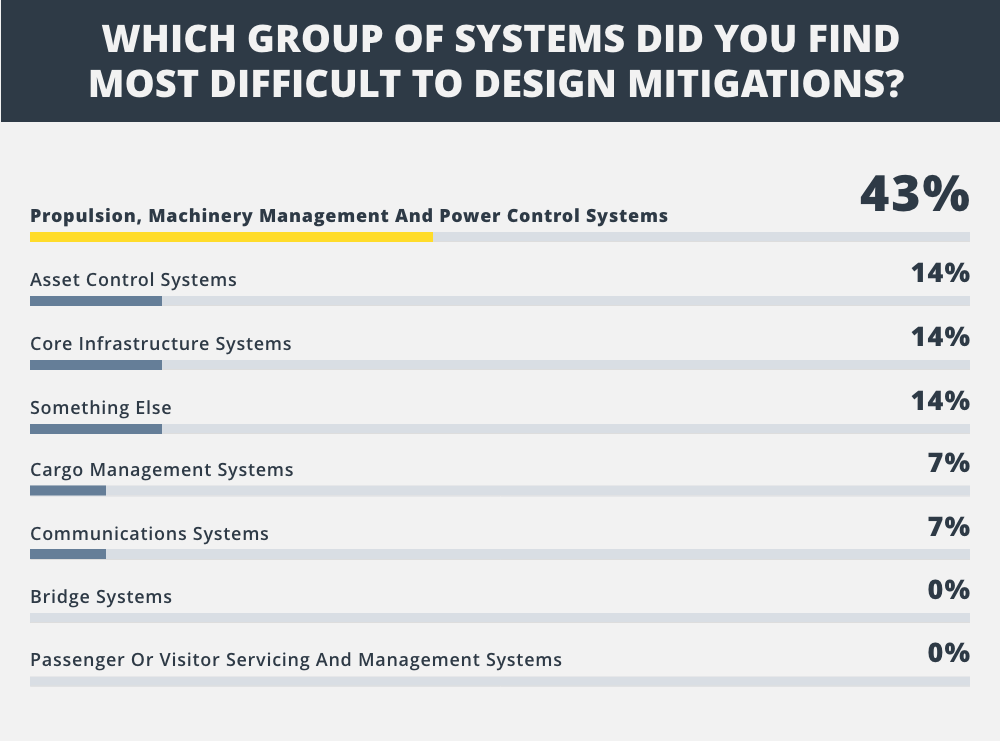
More crucially, there isn’t enough coordination across the supply chain. System manufacturers and integrators are simply not doing enough to provide fleet operators the assurance that the critical onboard systems are designed, integrated, managed and maintained in a way that ensures cyber resilience. Where challenged, they appear to be dragging their feet on being open and collaborative about addressing any vulnerabilities. Fleet operators attending the workshops intimated that they found cyber risks to propulsion and power systems the hardest to design mitigations for.
Tools to help you gain back some sleep
Many of these concerns can be addressed through a methodical approach to cyber risk assessment. If you are attempting to complete a risk assessment yourself, the new version 4 of the BIMCO Guidelines provide a theoretical framework as a starting point. From our experience, there are some practical challenges to using the framework. We address a number of these in a workshop to help fleet operators assess the cyber risk to shipboard systems.
Register interest for our next Cyber risk assessment workshop here
We are also continuously developing a number of other free cybersecurity tools that are useful for the shipping sector.
Provide thoughts on other areas we could develop tooling for here