Commercial ship managers have begun to notice how cyber risk management is affecting their operations.
To date, cybersecurity has been the domain of health, safety, environment and quality officers, IT or technical ship managers and generally ignored by the commercial team. The focus has primarily been about ensuring requirements under the Document of Compliance and Safety Management Certificate audits are fulfilled. However, the dynamics are changing.
With the volume of cybersecurity incidents at unprecedented levels in the maritime sector, charterers are increasingly concerned about protecting themselves from disruption and reputational damage. This is encouraging them to start drafting in clauses to explicitly call out responsibilities and obligations relating to effective cyber risk management in charterparties.
In June 2019, BIMCO issued a Cyber Security Clause 2019 that can be easily incorporated in maritime contracts. The clause makes explicit allocation between the parties of their respective cybersecurity responsibilities to maintain cyber hygiene, ensure readiness to respond to a cybersecurity incident and regularly review and maintain evidence of this preparedness. The clause envisages specific actions each party must take in the event of a cyber incident, including requirements to notify the other party of the cyber incident and to take active incident response and mitigation steps to avoid further disruption.
The BIMCO clause also makes explicit the responsibility to ensure any relevant third parties comply with the requirements. This extends the accountability to cover the actions and cyber readiness of the supply chain.
Where there are no explicit cybersecurity clauses in charterparties, the more proactive commercial managers have started examining implicit references to cyber security obligations, such as those in negligence clauses.
This makes cyber risk management no longer just the consideration of compliance and technical teams, but increasingly a commercial consideration.
Vessel profitability
At CyberOwl, we’re seeing one vessel cyber incident a day on average. In our case, we’re working hard with our customers to ensure these incidents do not result in disruption, financial or reputational loss. However, the volume of incidents we are experiencing should provide a sense of the present scale and pervasiveness of the cyber risk to shipping.
So why haven’t we heard of any cyber attacks resulting in dramatic collisions or loss of life in shipping?
Fortunately, the reality for now is that the way cyber incidents are manifesting is less sensational and more mundane. They fall into the category of likely, frequent but unreported. And they are chipping away at vessel profitability.
The most common implication of these cyber incidents can be best described as service interruptions and their cascading effects. Some examples include:
- Computing systems going down and out of service, forcing an unplanned vessel visit or inappropriate replacement of parts;
- Denial of service forcing crew and shoreside teams to revert to manual overrides that take 10 times as long to perform;
- Interruption to satellite communication bandwidth affecting seafarers’ ability to communicate with colleagues, friends and family at a time when seafarer welfare is under the spotlight; and
- Blackout periods in data and information used to drive commercial decisions, such as maintenance scheduling, voyage or fuel optimisation. This affects the return on investment in vessel digitalisation initiatives.
These are not “big bang” scenarios. They trickle into significant aggregates of wastage and unnecessary costs that is a growing stealth tax on the fleet operator. This is death by a thousand cuts.
To be clear, physical damage, safety or environmental incidents through cyber attacks is entirely possible. Commercial penetration testers and research institutions have repeatedly demonstrated how a motivated malicious actor could orchestrate a takeover of the command and control of a vessel to cause it to collide with another structure, fail in one of the maritime choke points or disrupt port operations with a little bit of effort. These low probability, high impact events should be factored into the calculation for risk management and risk transfer via
insurance.
Rising concerns
So it’s clear cyber risk management is becoming a commercial calculation for shipping. The question is how concerned should you be for your particular fleet?
This depends on the cyber risk profile of your maritime operations. Simplistically, the more business services, safety and environmental operations depend on data and computing, the higher your cyber risk profile. The higher your cyber risk profile, the more likely you would be subject to an attack and should therefore have more mitigations in place.
The difficulty for commercial managers is that cyber risk is often described in technical language. This makes getting an indication of the cyber risk profile of your fleet and maritime operations difficult to achieve.
However, asking the right questions can help bridge this technical divide. You should be listening hard both to the content and level of confidence in the responses to those questions, seeking evidence where possible.
As a commercial decision-maker for the vessel, your primary goal is to understand whether sufficient due diligence has been exercised by your organisation in order to protect itself from the key commercial risks related to cybersecurity. If not, you’re trying to understand the next best course of action, whether that is commissioning an internal audit or bringing in external expertise, if you don’t believe that exists internally.
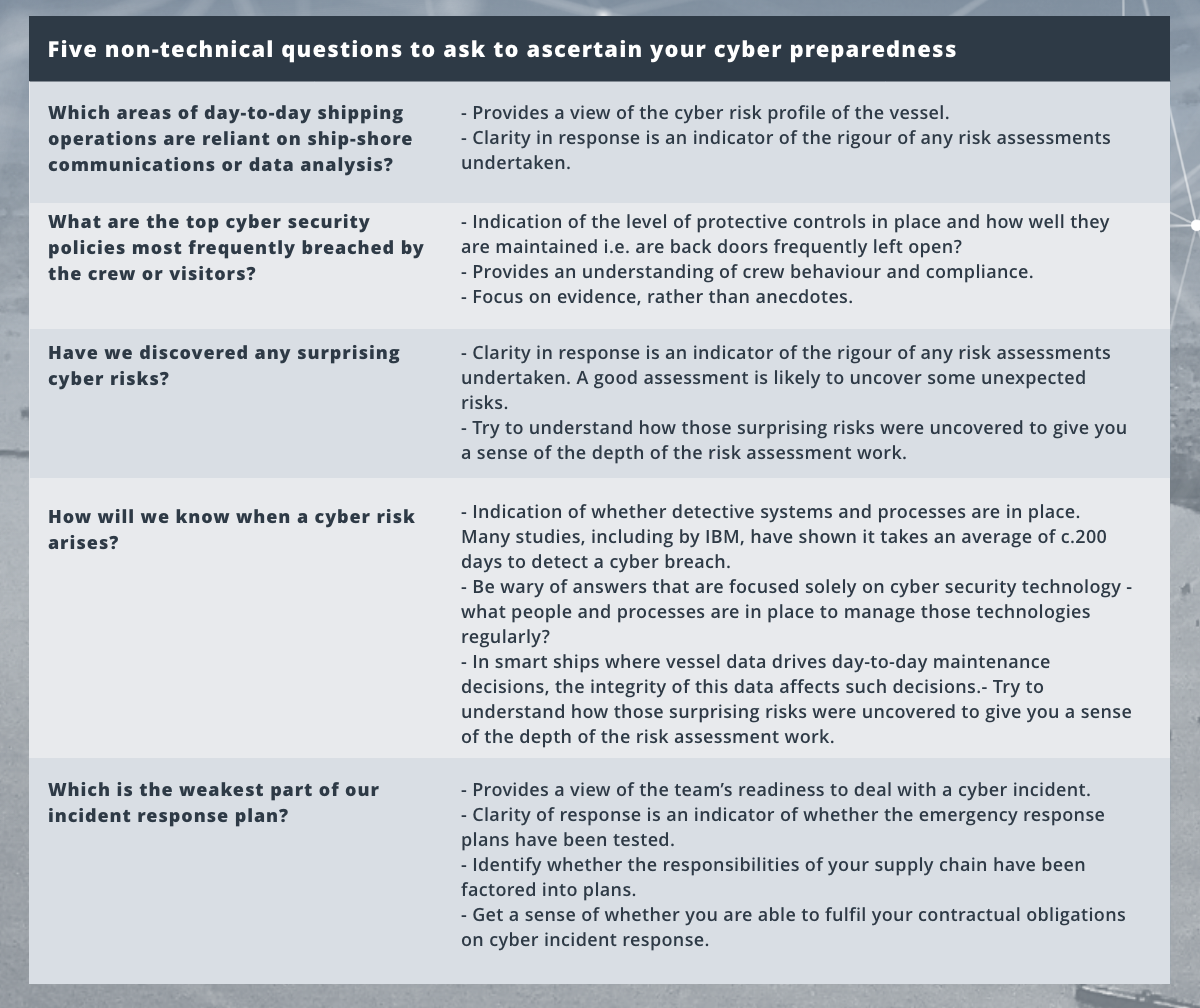
The table sets out 5 useful questions you should be asking your technical teams to glean an understanding of the cyber readiness of your shipping operations. Essentially, your line of questioning should be helping you gauge the following:
- How reliant your marine operations are on data and computing;
- Whether you can trust any cyber risk assessment completed;
- Whether there is evidence that any risk mitigation strategies have actually improved your cyber risk profile;
- The extent to which your organisation is aware and prepared to fulfil your commercial and contractual obligations on cyber risk management: and
- Whether your organisation has the internal capability to manage cyber risk effectively, or has otherwise sought appropriate external help.
 The discussion does not have to be deeply technical for you to achieve the goals above. The key is to ensure your organisation is prepared to protect against any commercial exposures related to cybersecurity, whether these are contractual obligations or issues affecting vessel profitability. At the very least, gain confidence that you’re on the path to being ready.
The discussion does not have to be deeply technical for you to achieve the goals above. The key is to ensure your organisation is prepared to protect against any commercial exposures related to cybersecurity, whether these are contractual obligations or issues affecting vessel profitability. At the very least, gain confidence that you’re on the path to being ready.


