Greek shipping operators are reeling from the Danaos supply chain ransomware attack but this case is only the latest in a series of such incidents. A key turning point came last December when a breach at SolarWinds led to a rare, emergency warning from US cybersecurity agency CISA. During the 14-month compromise at SolarWinds attackers introduced a backdoor into a product that was distributed to hundreds of their customers with major firms like Microsoft reporting unauthorised access to their systems as a result.
The incident became very real for us when, just days after the CISA warning, we coincidentally picked up suspicious network traffic between a client’s vessel and a range of SolarWinds IPs. Fortunately, our investigation quickly found that the traffic was from a legitimate IOT data logger which didn’t use the affected software… But it highlighted a common supply chain issue which is that our client had no idea their IOT supplier used SolarWinds infrastructure in their service.
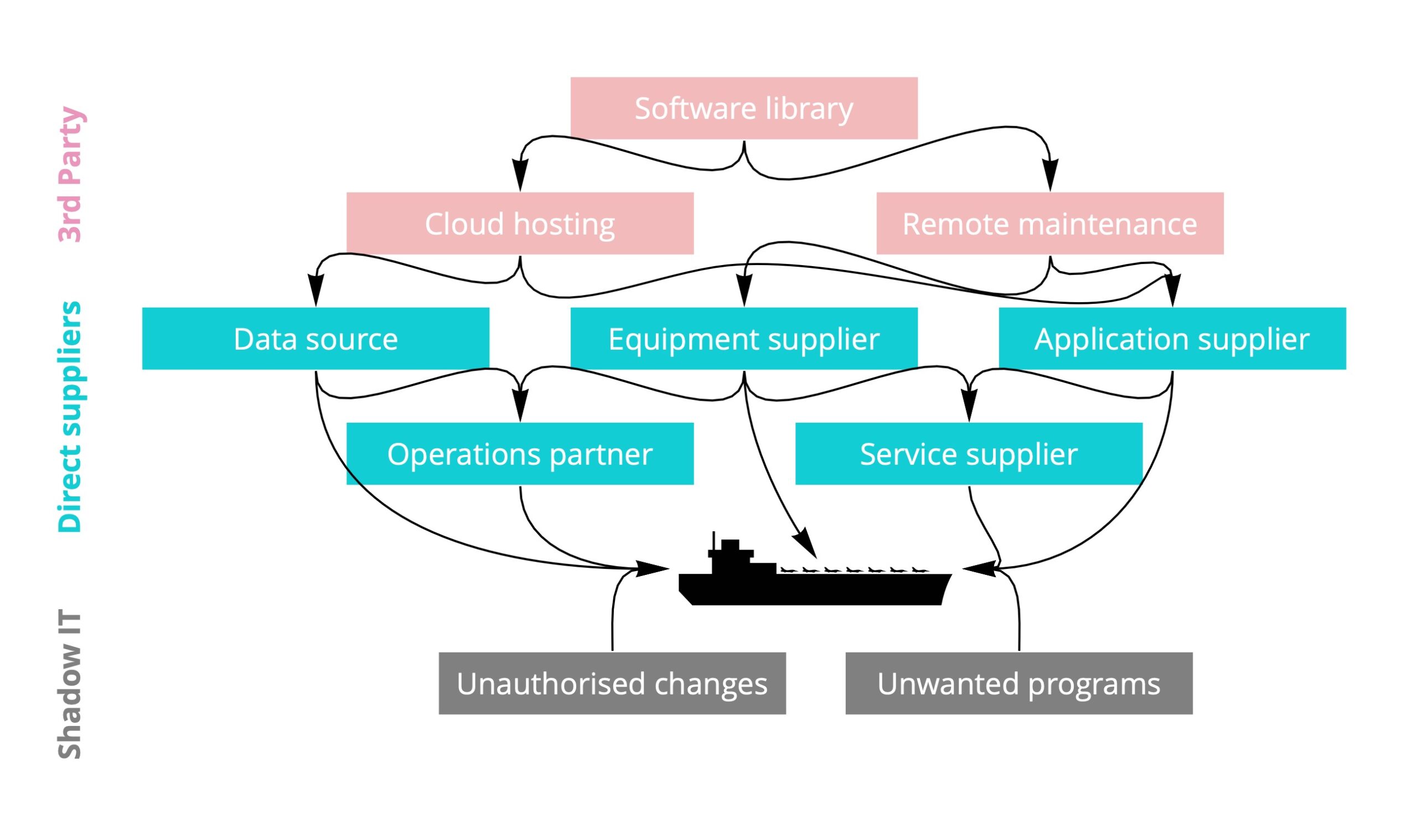
Fig 1. The data flows across the supply chain to vessels is often more complex than operators realise
Fortunately, the actor behind the SolarWinds breach didn’t deploy ransomware (reports suggest they were seeking confidential intelligence) but it underlined the potential far-reaching consequences of supply chain compromise: imagine if the access to Microsoft had been used to place a backdoor in Windows software… Ransomware gangs certainly took notice and research by EU cybersecurity agency ENISA predicts that 2021 will see four times as many supply chain attacks as last year.
Getting a grip on this threat is clearly critical for all businesses. And so last month we held a workshop in our Stop Talking Start Doing series which focussed on vessel supply chain security. Attendees discussed practical tips that can help reduce the risk.
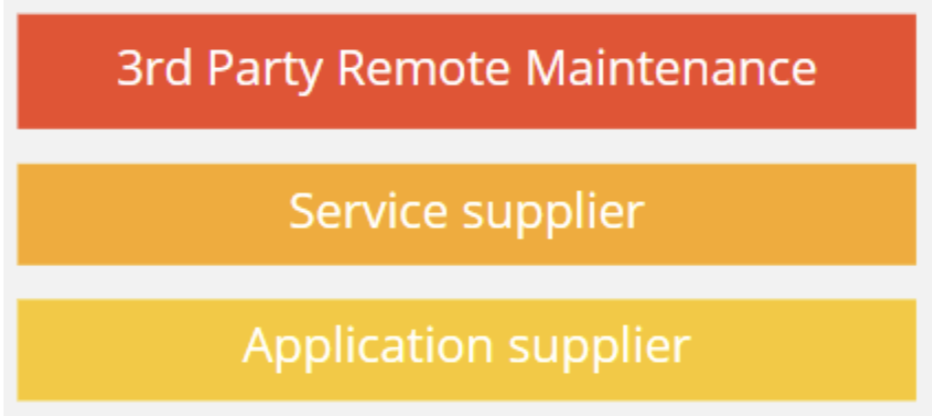 Fig 2. Workshop attendees top three supply chain concerns
Fig 2. Workshop attendees top three supply chain concerns
For instance, it’s agreed that an important prerequisite of supply chain management is an accurate list of your suppliers. But this isn’t always easy in practice with only a fraction of suppliers formally tracked by procurement. A tip shared at the workshop is to analyse your system logs to make a data-driven supplier list. With our help this is how our customer now knows that SolarWinds is in their supply chain.
Another practical use of monitoring data can address our workshop attendee’s top concern of 3rd party remote access. Having visibility of how and when remote access is used and managed can help mitigate the risk.
There is no magic bullet to supply chain risk or ransomware but lots of small steps combined with layers of controls and monitoring will help you get visibility of the risk and minimise the chance that you are significantly impacted by an attack.


